A positive reputation is a valuable asset. You deserve to be in control of what the internet says about you or your brand. We specialize in building, monitoring, and protecting digital reputations. Schedule time with our team to audit your existing digital presence and find ways to elevate and enhance your online impression.

What is Cyber Investigation?
Cyber crimes and attacks have significantly increased over the last 10 years. These issues include stealing sensitive private information about individuals and enterprises, disrupting business operations, a new era of digital financial fraud, and the manipulation of electronic records.
The consequences are manifold. First and foremost, cyber crimes impose additional costs on the victim and the economy at large. Furthermore, reputation damage and stress cause both psychological and physiological harm to the people affected.
Cyber investigations can solve these challenges. Blue Ocean Global Technology provides digital assistance that will support how you mitigate an existing challenge while also protecting you against future defamatory attacks. As part of this process, we identify and locate seemingly anonymous webmasters and perpetrators. While every cyber investigation case is sensitive and must be handled with care, it’s hard to communicate on the web without leaving an electronic fingerprint. The first step in our process after understanding the nuances of the case is to use every tool possible to locate and analyze critical evidence. This may include DNS/WHOIS lookups, metadata tracing, and Internet Protocol (IP) traps.
How It Works

Every piece of data on the internet is transmitted with an associated IP address attached to it. This address contains specific information about, but not limited to, its owner, web domain, computer name, and geolocation.
Because there is a limited time frame in which internet service providers store data from their subscribers, a cyber investigation team must act swiftly to first assess the situation and then explore all options. An embedded challenge is that there is no legal obligation for an internet service provider to comply with a formal request from a victim seeking identification or data preservation.
For this reason, a critical step in the cyber investigation process is retrieving the IP addresses of the parties in question. Internet service providers retain this information, and they can provide us with these IP addresses and other crucial data—often reluctantly after receiving a subpoena, warrant, or court order from our team.
Cyber Investigation Address?
Cyber Breaches
Cyber breaches are another serious and increasingly common issue. These incidents can range from attackers stealing customer financial information from websites to culprits that infiltrate networks and gain access to confidential corporate information. For severe cyber breaches, a thorough investigation process is required to understand what has caused the breach, identify the most effective way to fix the leak, and implement protective measures to ensure security in the future.
When a cyber breach does occur, we collect forensic data across networks and apply endpoint sensors to detect any malicious activities. We also use reverse engineering to highlight weak spots and determine the best course of action.

Fraud & Financial Crimes
Fraud and financial crimes include account manipulation, bribery, corruption, and identity theft. To provide clear evidence of fraudulent activities and allow for financial recovery, again, a forensic approach to cyber investigation is mandatory.
Providing Expert Evidence
We provide expert evidence for case assessments, prepare technical witness reports for legal submission, and educate the legal community through our continuing legal education (CLE) programs.

Cyber Investigation Experience: Cases & Solutions
Our global team of internet forensics, security experts, computer analysts, and cyber detectives offer services that include:
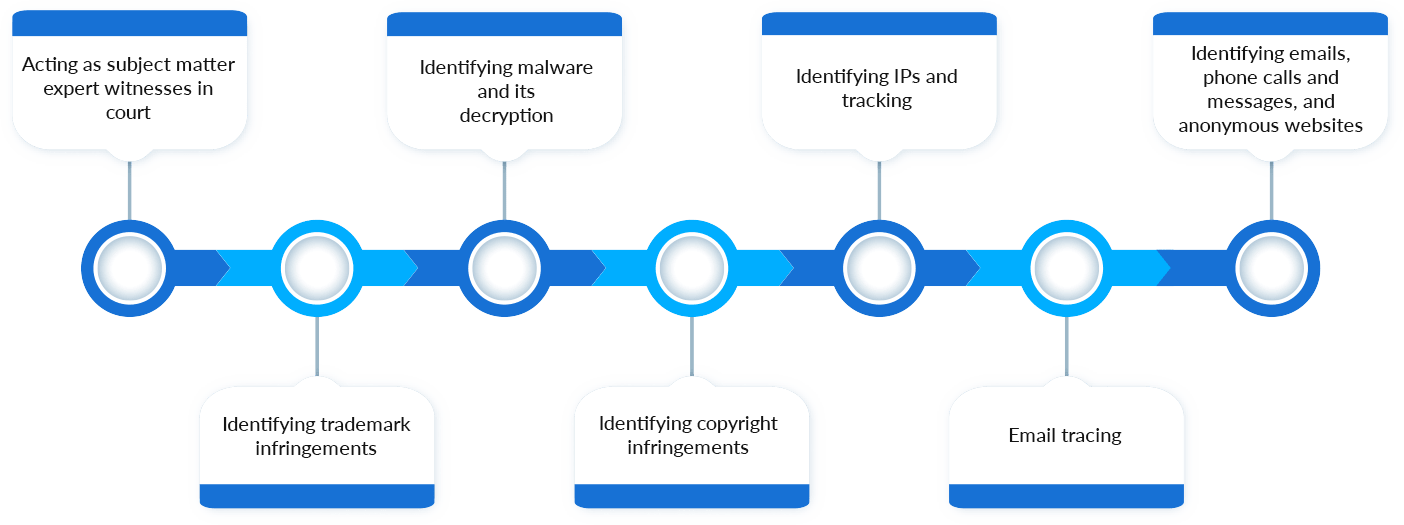
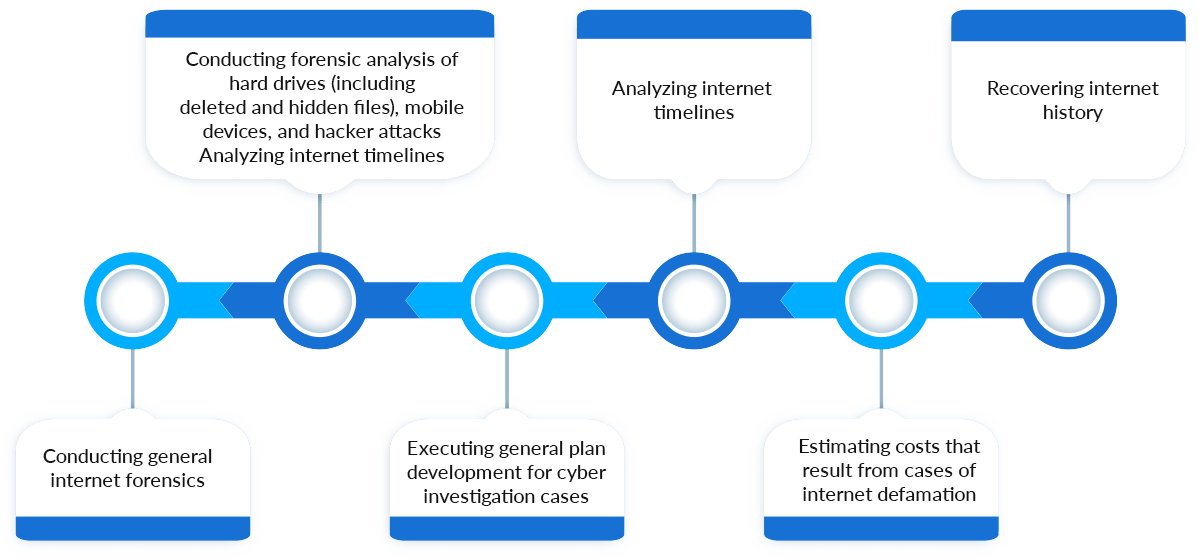
Please note that the list above provides examples of some of the types of cyber investigation services that we offer. Your situation may include several of the aforementioned service deliverables. Our cyber defamation expertise affords us an understanding of current laws and methods required to successfully manage a comprehensive cyber investigation.